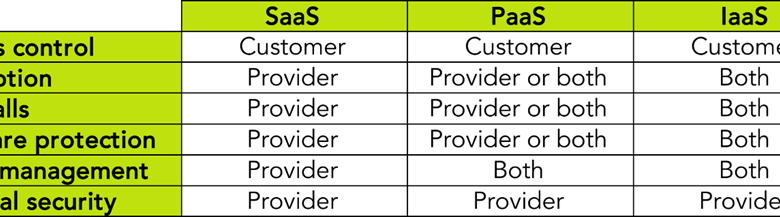
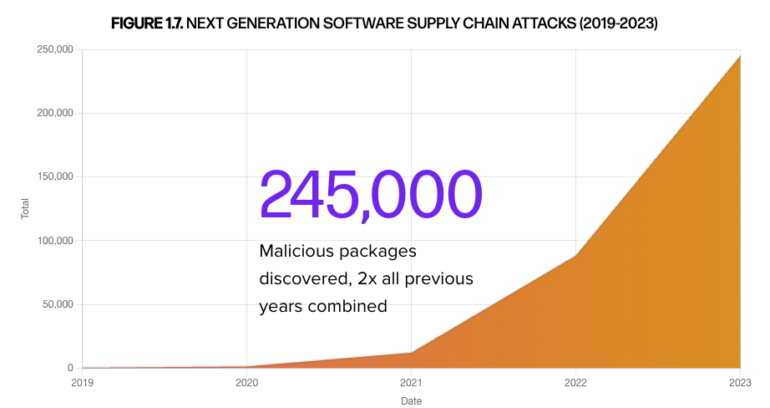
What to do when your ‘supply chain’ is really a ‘supply loop’ When I asked Bridget Kenyon – CISO (chief information security officer) for SSCL, lead editor for ISO 27001:2022 and author of ISO 27001 Controls – what she’d like to cover in an interview, she suggested supply chain security. I asked her whether she was thinking about the CrowdStrike incident (which happened just a few weeks prior). Bridget responded: “Not specifically. To be honest, supply chain security has been a perennial problem.” I sat down with her to find out more. In this interview Challenges of supply chain security
The post Strategies for Securing Your Supply Chain appeared first on IT Governance UK Blog.