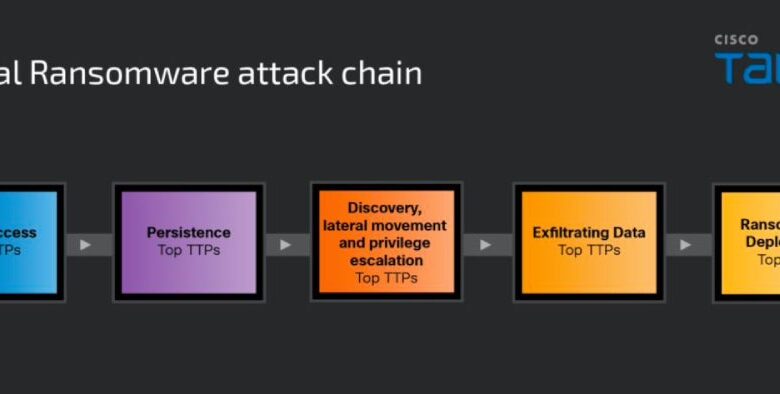
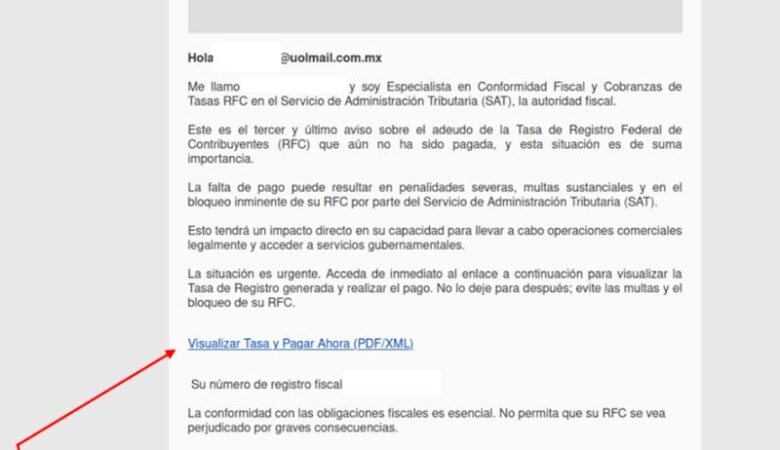
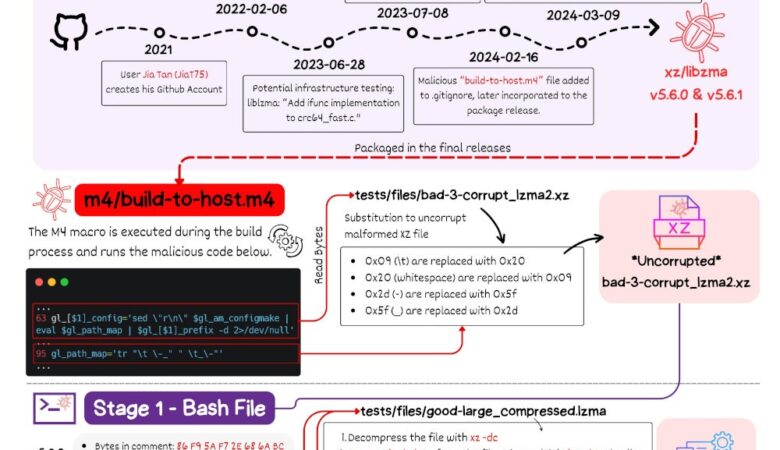
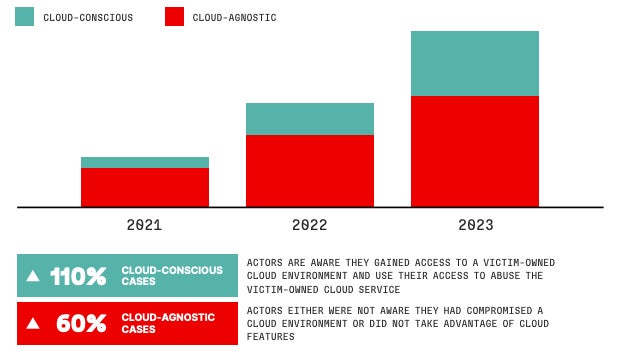
DoorDash has disclosed a social engineering-driven data breach exposing user contact details in four countries, raising concerns about delayed notification.
The post DoorDash Hit by Cybersecurity Breach, Millions of Users Potentially Exposed appeared first on TechRepublic.