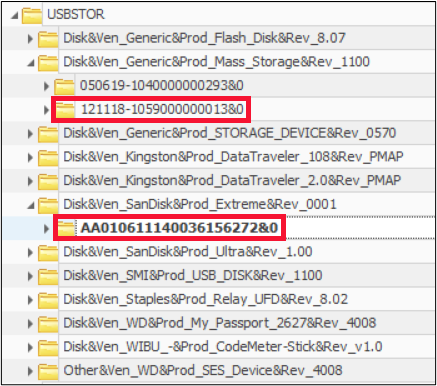
Evidence surrounding the use of USB devices is an often sought-after forensic treasure trove, due to its verbosity in the operating system, as well as the Windows Registry. The difficulty comes in attempting to make sense of all this data. When the many, disparate breadcrumbs of usage are pulled together in a coherent assemblage of user activity, the results can be shocking in their clarity.